Understanding Visual Hacking
Do you ever wonder how these major corporations get major data leaks or how these huge hacking leakshappen? While it is true there are talented hackers that can brute force their way into systems, many times it is something as simple as leaving a post-it note with your password out on your desk. This type of hacking commonly known as visual hacking or social engineering is getting more and more common, but there are definitely ways to prevent from being a victim.
Information About Hackers
This type of “low tech”security hacking is not new, and something that we hear about everyday. Security firms run tests all the time and are constantly able to get sensitive information just by looking around an office.
Hacker Studies
In a recent hacking study, security researchers were able to walk through an office without being questioned 5/50 times.In another study, 3M found that their researchers were able to obtain sensitive information 9/10 times in their study.
Hacker Protection
For starters, here are a few tips:
- Never keep hand written passwords out in the open on paper
- If you must, never keep passwordsin plain sight and always shred when you are done — never throw away
- Always watch over your shoulder when using a computer in a public place
- Always watch over your shoulder when using a mobile phone in a public place, particularly when you are entering a password
- Use a computer with a browser that allows you to browse in “private” or “incognito” mode when in a public place.
Even things such as confirmation pages after making a purchase can be a gold mine for hackers, always make sure when you are done making a payment that you close the window that you are using:
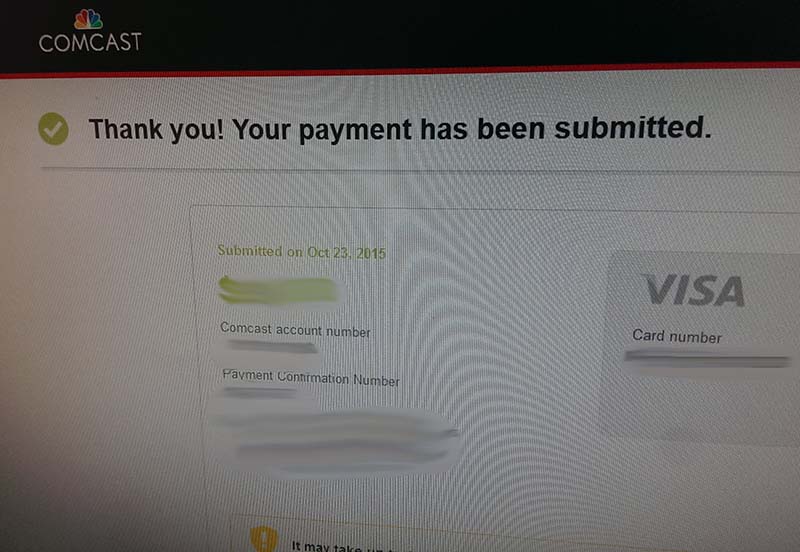
Always close windows on your computer with account information, particularly when you are in a public place.
Attackers can take this information and run wild with it, even if they don’t have your full information it is a starting point for them.
Another common pitfall are people that keep their passwords out in plain sight. One of our biggest pet peeves are people that leave their passwords taped to their monitor. This is a huge no!
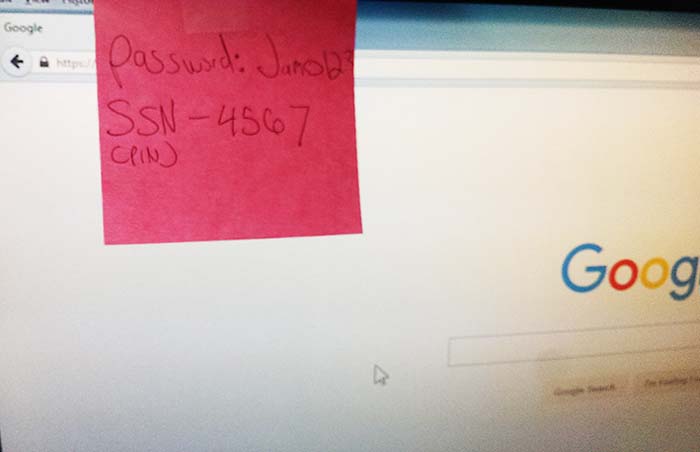
Never leave passwords or sensitive information out in plain sight.
Lastly, never leave your credit or debit card out in plain sight. It only takes a millisecond for a hacker to take a snapshot of your card and it is history from there.

Attackers can take a photo of your credit or debit card from up to a half mile away using modern day cameras.
Hackers now have extremely high powered cameras capable of reaching up to a half mile away to steal sensitive information.
If you must have sensitive information out in public, be sure to cover it up, using your body or another tool. In short, pretend as though you are taking a test and someone is trying to cheat from your answers.
The worst part about visual hackingis that you probably won’t notice it being done to you right away. Many visual attackers will start with a “weak link” i.e. a person or company with bad security policies. From there they will focus on that person or company making more mistakes until they build a victim profile and have enough information to hack your system or steal your identity.
If you have any questions, feel free to reach out to us at any time!
